| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: Mozilla Removes Avast, AVG Firefox Extensions Over Snooping Claims |
|
by Paul Arnote (parnote) Google Now Bans Some Linux Web Browsers 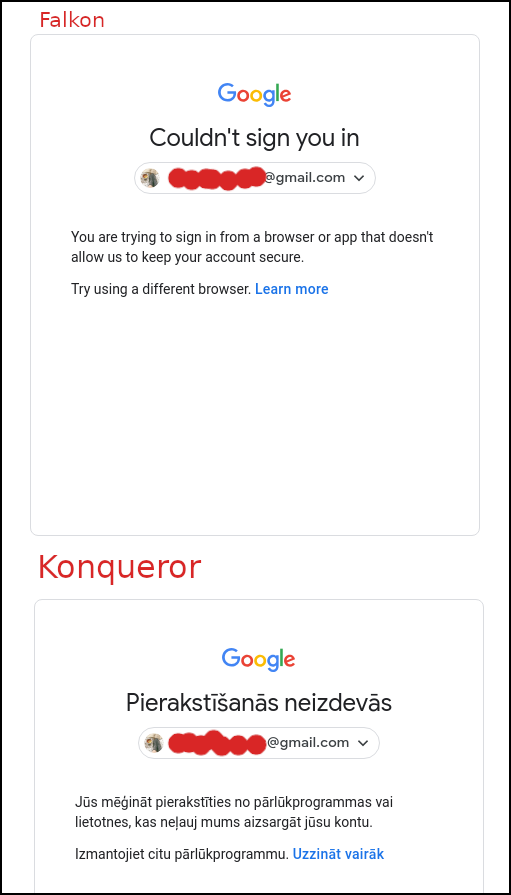 In its "infinite" wisdom, Google has now blocked certain Linux web browsers from accessing its services, according to an article on BleepingComputer. These Linux web browsers include Falkon, Konqueror and QuteBrowser. All but QuteBrowser are in the PCLinuxOS repository. Google asserts that they "may not be secure" ... as if logging into any Google service is like logging into some kind of fortress of security and privacy. The issue was reported on Reddit by u/onedoer. Ironically, there are also several replies in the Reddit thread of other users who have had no problem using the aforementioned Linux web browsers. BleepingComputers, in their independent tests, were able to confirm -- on multiple machines -- the inability to log into Google services on both Falkon and Konqueror. Clicking on the "Learn More" link reveals a number of reasons that Google provides for the possible block. They could include lack of support for JavaScript or having JavaScript support turned off, having unsecure or unsupported extensions installed, the use of automated testing frameworks, or the browser is embedded in a different application. There is only speculation about why the web browsers work for some users, but not others. Google has not yet responded to a query from BleepingComputers with an answer of any kind. Imagine that. Mozilla Removes All Avast, AVG Firefox Extensions Over Snooping Claims  Do you remember the free antivirus package AVG Free by Avast from back in your Windows days? Or, maybe you are aware of their current "antivirus" offerings for Linux. Well, for the past couple of years, Avast has made available four addons for Firefox. They are Avast Online Security, AVG Online Security, Avast SafePrice, and AVG SafePrice. In late October, Wladimir Palant, the creator or AdBlock Plus discovered that these addons were collecting WAY, WAY, WAY more information than was necessary to perform their duties. Take a look at the information collected, as pointed out from Palant's blog: The interesting fields were: uri: The full address of the page you are on. title: Page title if available. referrer: Address of the page that you got here from, if any. windowNum and tabNum: Identifier of the window and tab that the page loaded into. Initiating_user_action windowEvent: How exactly you got to the page, e.g. by entering the address directly, using a bookmark or clicking a link. visited: Whether you visited this page before. locale: Your country code, which seems to be guessed from the browser locale. This will be "US" for US English. userid: A unique user identifier generated by the extension. plugin_guid: Seems to be another unique user identifier. browserType and browserVersion: Type (e.g. Chrome or Firefox) and version number of your browser. os and osVersion: Your operating system and exact version number (the latter only known to the extension if Avast Antivirus is installed). All of this information, and more, was transmitted to Avast and AVG servers. According to a gHacks article, data was sent whenever a user opened a page or switched tabs, as well as every single click on a search page. If the above revelation didn't unnerve you, take a look at this assertion on Palant's blog page: The data collected here goes far beyond merely exposing the sites that you visit and your search history. Tracking tab and window identifiers as well as your actions allows Avast to create a nearly precise reconstruction of your browsing behavior: how many tabs you have open, what websites do you visit and when, how much time do you spend reading/watching the contents, what do you click there and when do you switch to another tab. All that is connected to a number of attributes allowing Avast to recognize you reliably, even a unique user identifier. Palant reported the excessive data collection to Mozilla, and received a polite "thank you" for his notification. Then, in less than 24 hours, Mozilla quietly removed the Avast and AVG addons from the Mozilla addon repository, stopping short of putting them on the blacklist (which would have inactivated/removed every installed copy on users' machines). In response, Avast provided the following statement: We have offered our Avast Online Security and SafePrice browser extensions for many years through the Mozilla store. Mozilla has recently updated its store policy and we are liaising with them in order to make the necessary adjustments to our extensions to align with new requirements. The Avast Online Security extension is a security tool that protects users online, including from infected websites and phishing attacks. It is necessary for this service to collect the URL history to deliver its expected functionality. Avast does this without collecting or storing a user's identification. We have already implemented some of Mozilla's new requirements and will release further updated versions that are fully compliant and transparent per the new requirements. These will be available as usual in the Mozilla store in the near future. Avast claims, via a BleepingComputer article, that it had less than 12 hours to resolve the issue. As of the writing of this article (late December), the issues appear to have been resolved, and the Avast and AVG addons are once again available in the Mozilla addon repository. Avast provided the following statement to gHacks: "Privacy is our top priority and the discussion about what is best practice in dealing with data is an ongoing one in the tech industry. We have never compromised on the security or privacy of personal data. We are listening to our users and acknowledge that we need to be more transparent with our users about what data is necessary for our security products to work, and to give them a choice in whether they wish to share their data further and for what purpose. We made changes to our extensions including limiting the use of data and these changes are explained clearly in our Privacy Policy. Our browser extensions Avast Online Security and AVG Online Security are back on the Chrome Store, and on the Mozilla Store (since 12/17). It's important to us that users understand that we're listening to concerns about transparency and data use, and striving to do better and lead by example in this area." Through at least the beginning of this "event," the Avast and AVG extensions remained available through the Google Play Store. Avast's response seems to indicate that at some point, the extensions were also removed from the Google Play Store. Firefox Launches Firefox Private Network Browsing  (From the Mozilla blog) In September, we (Mozilla) introduced the beta release of our Firefox Private Network (FPN), an extension which provides a secure, encrypted path to the web to protect your connection and personal information when you use the Firefox browser. Since then, we've received feedback from our beta testers on how they're using FPN, its protections, and we learned about websites that weren't compatible as well as connection issues. This allowed us to quickly identify and fix bugs, and ensure a stable product. As we continue our beta testing, we are considering various ways to bring additional privacy protections to our users. Today we're announcing an additional beta test for US-based Firefox account users who didn't get a chance to get in the initial group, and are interested in testing FPN. In the next phase of our beta, we are offering a limited-time free service that lets you encrypt your Firefox connections for up to 12 hours a month. With the holidays around the corner, the FPN couldn't come at a more convenient time. We know people are traveling and might have to rely on an unsecured public Wi-Fi network, like the one at the airport, at your local coffee shop, or even at your doctor's office. FPN provides encrypted internet traffic thus giving you peace of mind whenever you're using our browser. This limited-time free service is currently available in the US on the Firefox desktop browser and you'll need a Firefox account to try the service. You can sign up directly from the extension which can be found here. For those looking to extend their protection beyond the browser, you can now sign up to be one of the first to experience the newest member of the FPN family. This month, Firefox account holders can request invitations to experience device-level protection with our new full-device VPN (virtual private network). Join the waitlist and if you're eligible, we'll follow up with a link to access the VPN at an introductory price of $4.99 per month. Currently the VPN will be available for Windows 10 only, and like the rest of the FPN, it is only available to US-based Firefox account holders. Pricing and platform availability will continue to evolve and we look forward to hearing your feedback. Firefox Says NO To Fingerprinting  One of the topics at this past summer's Google IO developer conference was how to help preserve user privacy by blocking "fingerprinting." Well, Firefox just did an end run around Google, and has blocked fingerprinting. So exactly what is fingerprinting? Virtually everyone knows what cookies are when it comes to web browsing. Cookies are easy to block, and many sites give you the option to opt out of them. But fingerprinting is different. It collects basic information from your browser session and your computer, using it to create a unique "fingerprint" of you. Included may be the make and model of your computer, how much RAM you have, processor identification, web browser, screen resolution, your timezone, the language you use, the combination of third-party extensions you have installed, and even the fonts installed on your system. From all of that, it's rather easy to create a very specific and unique profile that can be used to track you across the web. Unfortunately, it happens without most users even realizing that it's happening, and there are mostly no mechanisms to allow a user to opt out of fingerprinting. 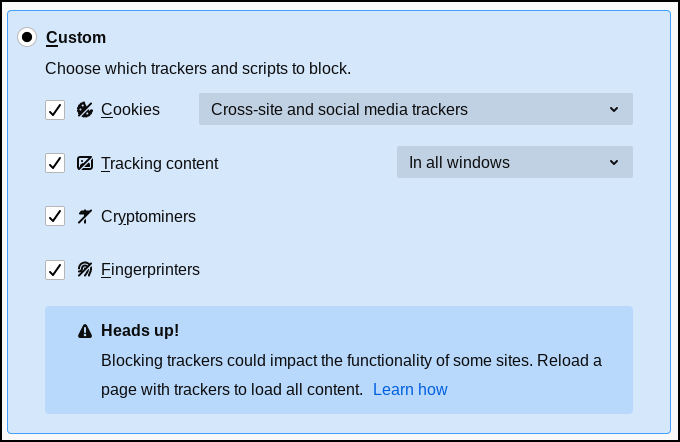 Starting with Firefox 72, due out later this month, Firefox will block fingerprint trackers by default. But, you don't have to wait until Firefox 72 to block fingerprint trackers. You can enable it now. In Firefox versions as early as 70, you can turn on protection against fingerprint trackers. Go to Preferences, then Privacy & Security. Under the "Enhanced Tracking Protection" section, select either "Strict" or the "Custom" setting. Under the "Custom" setting, you can choose to allow or disallow certain types of trackers. Strict just blocks them all. Even though turning on all the tracker and script blockers is basically the same as just selecting the Strict setting, I prefer to have the option of turning things off and on as I see fit. Also, the custom setting gives me a little more control of how strict I want to get about blocking trackers and scripts. Make Sure Your Password Isn't Among The 100 Worst Passwords Of 2019  SplashData has released their list of the top 100 worst passwords of 2019. The battle for the absolute worst password wasn't really a battle or competition -- it was the same as the worst password of 2018: 123456. Some variation of the worst password (123456) occupies six of the ten worst passwords in the list. You can view the worst passwords, ranked 50 through 100, here. To view the top 49 worst passwords, go here. Over and over, users don't seem to be getting the message about using strong passwords to protect their data and privacy. Here at The PCLinuxOS Magazine, we've run numerous articles about passwords, password security, and methods to employ in creating secure passwords. To summarize, be sure to follow a few simple rules for the creation and use of passwords. First, don't reuse passwords between sites and programs that ask for one. Use ONLY passwords that are unique to each site. Second, don't use birthdays, street addresses, and names of your spouse, children and pets ... basically, anything that is easily associated with you. Third, use a method of generating passwords that is known only to you. This means that you can use a "base" password that is tailored/altered for each site you need a password for, as an example. Fourth, mix uppercase letters, lowercase letters, numbers and punctuation marks in your password creation process. It makes it much more difficult for hackers to break your password. It's YOUR data. It's YOUR privacy. No one else is going to bother to protect it for you, so that is your responsibility, and yours alone. The temptation to gain access to your privacy and data is too tempting to allow someone else to be responsible for. Don't make the mistake of underestimating the value of your data and privacy. PCLinuxOS Roundup  AT THE BEGINNING OF 2019, Google announced their Manifest V3 plans, which ultimately broke several ad blocker extensions, and made them a lot less effective. Now, users are raging against Google for their web API called getInstalledRelatedApps. It has been in development since 2015, and has been available to experiment with since Chrome 59 came out in 2017. Basically, the API lets developers determine if their native app is installed on your device. The outrage comes from the potential to violate users' security and privacy, according to an article on Forbes. The potential for abuse is ripe, and given Google's oversight (or lack thereof) of the Google Play Store, users have every expectation that Google's oversight of the use of this API is most likely going to be sorely lacking. CYBERSECURITY ANALYSTS AT THE NEWLY FORMED SENTINEL LABS claim to have found some of the first hard links between the crimeware organization TrickBot and Lazarus Group, the cyberwarfare division of the North Korean military's Reconnaissance General Bureau, according to an article on TechRepublic. ACCORDING TO AN ARTICLE ON DECRYPT, hackers have a new way to surreptitiously mine Monero cryptocurrency on your computer. They will drop malware somewhere on your computer, where it remains unknown to the user. The malware itself doesn't contain malicious code, but when activated by a series of commands, it will start using the infected user's computer to mine cryptocurrency. The code lies in an inactive state, remaining undetected, until it is activated by the series of commands. It then sends the mined Monero to a wallet controlled by the hacker. HOW DO YOU FEEL ABOUT YOUR SMARTPHONE TRACKING YOU everywhere you go, and monitoring everything you do? If you think it isn't a big deal, and you're willing to "live with it" as it currently exists just for the convenience that your smartphone provides, you need to read this introductory opinion article from the New York Times. It's worse than you think, and they provide ample evidence about just how bad the situation really is. This article will likely scare the bejeezus out of you, as it should. This is the inaugural article of a seven article series that is, to say the least, eye opening. |



