| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
From The "I Told You So" Department #1 |
|
by phorneker For the past two months, I mentioned that just because we use PCLinuxOS does not mean that we are completely safe and secure from the common problems faced by Windows and Mac OS-X users. This past two weeks brought two new terms to the Linux scene: Scepter and Meltdown. I mentioned that we were lucky about malware not affecting Linux users. Though Scepter and Meltdown are actually design flaws in microprocessors built over the past twenty years, they pose security risks now affecting Linux users. (Note that the title of this series is called From the "I Told You So" Department.) Thankfully, Texstar has patched the 4.4, 4.9 and the current kernels to avert any potential security and safety problems that would have occurred with Meltdown and Scepter. Hence, it is imperative that we update the kernel to the latest version available in the repository. To update the kernel in PCLinuxOS, open Synaptic, click on Reload, then click on Status. 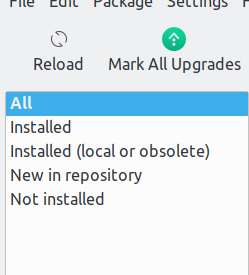 If an updated kernel has been uploaded to the repository, it will be found under New in repository. Select any package with kernel in its name. Both the kernel and its development package will be selected. Click on Apply to install the new kernel. Synaptic will automatically update the bootloader and show you the changes. Then reboot your PCLinuxOS installation (with the updated kernel) to ensure the changes have been made. Back to the topic of Scepter and Meltdown, these design flaws have been a part of Intel's processors for the past twenty years. These design flaws allow cyber intruders to remotely obtain personal information (including passwords) without your knowledge, or even without logging in to your PCLinuxOS machine, especially after a system update that requires a reboot (such as a Plasma desktop upgrade). This means any machine with a Intel processor built since 1998 has this design flaw. Having said that, this brings up some serious issues. As revealed in the MS vs DOJ Antitrust Case of 1998, Microsoft made secret deals with computer manufacturers back in 1990 to include only Windows on the hard drive, and to not offer any alternatives available at the time such as IBM's OS/2 (now Arca Noae's ArcaOS) and Solaris. What was Intel's role in that? The original IBM Personal Computer (Model 5151) was built on an Intel 8088 processor rather than a Motorola 6502 or 68000 processor. As the market grew for personal computers, businesses and individuals alike wanted compatibility with the IBM Personal Computer, but wanted that compatibility at a lower cost. (Rather obvious isn't it?) By the middle 1990s, most personal computers in the market were equipped with Intel processors and Windows installed on the hard drives (supposedly making it easier for the customer, but I never believed that). The result of all of this was the Wintel monopoly. This meant that Microsoft and Intel had virtually complete control of the hardware and software market. This also meant that if any problems manifested themselves, both companies could well sit on the problem for months, even years at a time before anything was done about them. Sound familiar? Thankfully, the introduction of Linux and the open source concept to the mainstream at the Fall Comdex 1998 intended to change all of that. The idea behind the open course concept (as well as the Debian social contract) is to make sure there is transparency in everything technology related. That is, any problems that manifest themselves should be resolved as soon as possible and not hidden from the public. Why is this important? Look no further than the WannaCry malware and what it did to a hospital system in the UK. When computers are used in critical setting such as a hospital or a nuclear plant, we want these systems to be working properly, and proper precautions taken, and we want the integrity of these systems to not be compromised. In other words, these computers should be maintained as if our lives depended on it, because they do! The question here is this: Why did Intel hide this design flaw from the public for the past twenty years? Was it gross negligence on Intel's part, or was it blatant dishonesty. Common practices in monopolies over the past two centuries suggest the latter. To hide a problem for that long and make money off of it is clear cut evidence that dishonesty is the case. Thankfully, we have fixed the problem in software (as Texstar did with the kernels), and it is up to us to apply the fixes. What Intel wants businesses to do is to replace all older computers with new computers. One could argue that this statement was a result of a declining market for personal computers, mainly because of the growing market for mobile devices. Even then, the mobile device market has its share of growing pains as well (in the form of design flaws and malware now targeted iOS and Android devices). What I speculate from all of this is that the consumer is tired of all the b******* coming from the tech companies (both hardware and software aspects, as well as the networks they connect to) and particularly from Silicon Valley. It is not just me who is speculating this. Simply visit Richard Stallman's personal website (http://stallman.org) and his views on technology. He has been contributing to computing since the 1970s, and is one of the founding fathers of the open source movement. Also, check out the Free Software Foundation website (https://www.fsf.org) as well as their Defective by Design website. As we cannot rely on our government (state and federal levels) to do its job of protecting consumers (where is Ralph Nader when we need him?). It is up to us to resolve these matters, and to be able to make our own decisions with integrity, and most of all with common sense. Also, I have my views on the Microsoft vs DOJ Antitrust Case of 1998 archived in the Internet Archive. So, what do I do to protect myself and my cyber assets? First, I do not run my laptop 24/7. By that, I mean that the machine does not have to be powered on all the time. In fact, it is powered up when I need to have it on, and when I do not need to use the laptop, it is powered down. By not having the machine powered on all the time, it is difficult for would be cyber criminals to plan their attack … and that is a good thing. Second, there is a cliche that has been around for decades, that still applies today. If an offer seems too good to be true, it probably is. Be it in the form of physical junk mail, or an ad infested email, the principle still applies. Same with unsolicited phone calls. Those go direct to voicemail. If it is important, the caller will leave a message. If not, it was probably not that important (or even legitimate) anyway. Third, if I cannot tell if a story is legitimate or is "fake news", assume the latter, and don't trust anything until I can verify beyond a shadow of a doubt that the information is true. For those of you who remember the TV miniseries "Centennial" (around 1980), there is a quote that could well apply today. It is one of the last quotes found in the last episode towards the end of that episode. "We have got to look at our past, and go back to basics, if we expect to have a future." It could not be more true today. |