| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Short Topix: U. S Gov't Once Again Requests iOS Back Door |
|
by Paul Arnote (parnote) Microsoft Commandeers 50 N. Korean Hacking Sites By Court Order  In a bold move that will end up protecting users everywhere for all platforms, Microsoft has taken control of 50 domains believed to be used by the North Korean hacking group commonly referred to as Thallium, according to a blog report on Microsoft's site. U.S. District Court documents were unsealed on December 27, 2019 that detail the steps that Microsoft has undertaken to disrupt cyberattacks originating from the Thallium hacking group. As a result, those 50 sites will no longer be able to be used to launch cyberattacks. The attacks were mostly "spear phishing" attacks. They would attempt to trick users into logging into a fake Microsoft security account to fill out information about their accounts, and into revealing their account credentials. By combining publicly available information gleaned from social media accounts, the Thallium group of hackers was able to make a rather believable case for the possibility of a user's account becoming compromised. They also employed techniques that might go undetected by the average non-tech savvy users, such as using an "r" and an "n" closely spaced to represent the first "m" in the "microsoft.com" website address. From the Microsoft blog entry: Microsoft's Digital Crimes Unit (DCU) and the Microsoft Threat Intelligence Center (MSTIC) have been tracking and gathering information on Thallium, monitoring the group's activities to establish and operate a network of websites, domains and internet-connected computers. This network was used to target victims and then compromise their online accounts, infect their computers, compromise the security of their networks and steal sensitive information. Based on victim information, the targets included government employees, think tanks, university staff members, members of organizations focused on world peace and human rights, and individuals that work on nuclear proliferation issues. Most targets were based in the U.S., as well as Japan and South Korea.... This is the fourth nation-state activity group against which Microsoft has filed similar legal actions to take down malicious domain infrastructure. Previous disruptions have targeted Barium, operating from China, Strontium, operating from Russia, and Phosphorus, operating from Iran. These actions have resulted in the takedown of hundreds of domains, the protection of thousands of victims and improved the security of the ecosystem. Be vigilant, folks! There are bad actors out there everywhere who want access to your private information and accounts. Your data is truly the currency d'jour, especially among cybercriminals, and you are the best resource for protecting that data. Add A "Real" Search Box To Google Chrome's New Tab Page Google placed a search bar on the new page tab in Google Chrome in 2012. But, have you noticed that the search bar in the new page tab is fake? Yep. It is. In a plain, unmodified installation of Google Chrome, the search bar displayed on the new page tab simply redirects its output to the address bar. This makes it no different than performing the search from the address bar in the first place. It doesn't matter much if you have Google or some other search engine set as your default, either (Bing, if selected, performs pretty much as it would if you went to the Bing homepage, though). 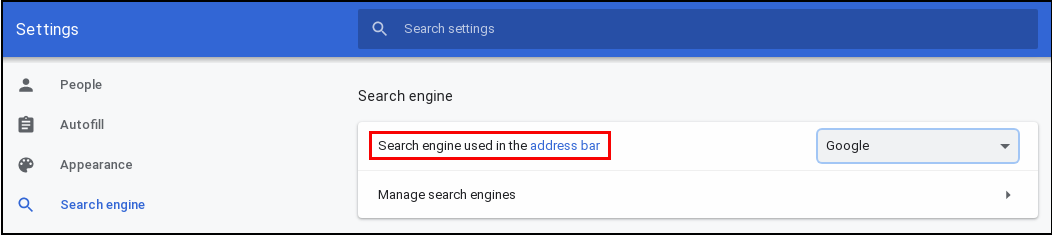 Here's why this happens. Go to Chrome's hamburger menu, and select "Settings." Go to the "Search Engine" selection on the left side of the screen. Notice in the image above, the setting explicitly says "Search engine used in the address bar" (highlighted by the red box). But, according to an article on ghacks.com, you can now return a REAL search bar to the new page tab by making a small change to your installed copy of Google Chrome. It won't matter which search engine you use as your default, either. This means that your search criteria aren't just redirected to the address bar. 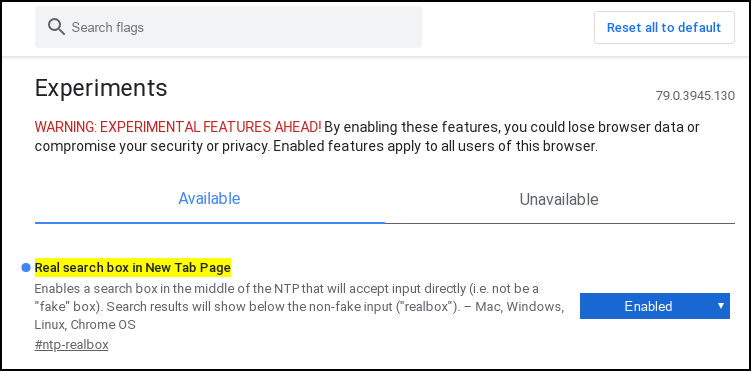 First, open a new tab. Type "chrome://flags/#ntp-realbox" on the address bar, then press enter. You should see something like the image above. At the right, there is a dropdown selector (mine is already "Enabled"). The choices are default, enabled or disabled. There! That is all there is to it. Now, the search bar in the new page tab actually works as you expect it to, instead of just redirecting to the address bar. The image below shows the search bar actually performing its intended job.  ProtonMail Adds Encrypted Calendar  You've probably heard about the secure email solution called ProtonMail. If you haven't, it is a direct competitor to Google's email service, commonly referred to as Gmail. ProtonMail is encrypted over its entire delivery path. Google claims to have stopped scanning users' emails for keywords to use for serving ads back in 2017, but then who can be completely sure? Google, facing recurrent bouts with public outrage over its actions (and having dropped the "Do No Evil" credo), has become an increasingly secretive corporation. The transparency upon which Google was founded has become about as opaque as iron. With ProtonMail, there is no question about your email remaining private ... just like your snail mail. ProtonMail (company name is Proton Technologies AG) is based out of Geneva, Switzerland, and is subject to Switzerland's stricter-than-most-other-countries privacy laws. Their mail servers are all located in Switzerland, so there's little to no fear of the company's servers being commandeered by some rogue nation in some yet-to-come revolution or uprising. According to an article at The Verge, ProtonMail has just began offering an encrypted calendar to all ProtonMail users on a paid plan (currently $4/€4 per month, billed annually at $48/€48). It is called ProtonCalendar, and it is in the early beta stages. It is also only currently available via the web interface, although dedicated iOS and Android apps are also in the works. ProtonMail claims that some companies will scan your calendar entries to target ads to you. A Google spokesperson told The Verge that they do not currently scan calendar entries to target ads to you. The Verge followed up and asked if Google ever has used calendar entries to target ads to users, but Google has yet to respond.
From the ProtonMail blog announcing ProtonCalendar:
"A calendar is more than just a tool. It's a record of the moments that make up your life -- your big meetings, your gatherings with friends, and children's birthdays. For the longest time, to easily organize these events, you had to let large corporations monitor these special moments. These companies snoop on your calendar and use that information to inform their advertising.
...
"We believe everyone has the right to plan dinner with friends without announcing to Google who will attend. For that reason, once ProtonCalendar is publicly released, a basic version will be available to all ProtonMail users (including Free users) while paid Proton users will benefit from additional functionality."
U.S. Gov't Once Again Requests iOS Back Door  A widely reported incident where a Saudi Air Force cadet shot and killed three U.S. servicemen, and wounded eight others, at the Pensacola, Florida naval air station before being shot and killed himself by a police officer is being called an act of terrorism. The cadet had two iPhones in his possession at the time of the incident. In shades of 2016, when the San Bernardino, California shooter had an iPhone 7 in his possession, the government asked Apple to provide government officials "backdoor" access to the contents of the phone. U.S. Attorney General William Barr has renewed that request, and Apple's response is the same as it was the first time ... no way. The Pensacola cadet had two iPhones in his possession: and iPhone 7 and an iPhone 5. The shooter placed one iPhone down on the ground and put a round through it, but the FBI has been successful in reconstructing the damaged phone. The problem comes about because of a security feature on the iPhones. If the wrong PIN is entered more than six times in a row, all of the data on the phone is automatically deleted, effectively rendering most brute-force attacks worthless and futile. The 2016 case by the U.S. government against Apple never went before the courts, since the FBI enlisted the services of Israel-based Cellebrite to crack the iPhone encryption. In that case, Apple refused to comply with a court order to crack the iPhone encryption. Apple has remained steadfast in its refusal to install a backdoor for the "good guys," insisting that such a backdoor can be equally exploited by the "bad guys," and causing a nightmare for everyone involved. To think that a backdoor for the "good guys" won't be discovered by and exploited by the "bad guys" is far beyond naive. Here is Apple's complete response to the charges leveled by U.S. Attorney General William Barr: We were devastated to learn of the tragic terrorist attack on members of the US armed services at the Naval Air Station in Pensacola, Florida on December 6th. We have the greatest respect for law enforcement and routinely work with police across the country on their investigations. When law enforcement requests our assistance, our teams work around the clock to provide them with the information we have. We reject the characterization that Apple has not provided substantive assistance in the Pensacola investigation. Our responses to their many requests since the attack have been timely, thorough and are ongoing. Within hours of the FBI's first request on December 6th, we produced a wide variety of information associated with the investigation. From December 7th through the 14th, we received six additional legal requests and in response provided information including iCloud backups, account information and transactional data for multiple accounts. We responded to each request promptly, often within hours, sharing information with FBI offices in Jacksonville, Pensacola and New York. The queries resulted in many gigabytes of information that we turned over to investigators. In every instance, we responded with all of the information that we had. The FBI only notified us on January 6th that they needed additional assistance -- a month after the attack occurred. Only then did we learn about the existence of a second iPhone associated with the investigation and the FBI's inability to access either iPhone. It was not until January 8th that we received a subpoena for information related to the second iPhone, which we responded to within hours. Early outreach is critical to accessing information and finding additional options. We are continuing to work with the FBI, and our engineering teams recently had a call to provide additional technical assistance. Apple has great respect for the Bureau's work, and we will work tirelessly to help them investigate this tragic attack on our nation. We have always maintained there is no such thing as a backdoor just for the good guys. Backdoors can also be exploited by those who threaten our national security and the data security of our customers. Today, law enforcement has access to more data than ever before in history, so Americans do not have to choose between weakening encryption and solving investigations. We feel strongly encryption is vital to protecting our country and our users' data. Apple is supported in its efforts to resist the government's request by the ACLU and the EFF, among other groups concerned about user privacy. Even more recently, it was revealed that Apple backed away from a plan to encrypt the iCloud backups after the FBI complained in 2016. To date, the iCloud backups remain unencrypted. It has been widely reported that Apple changed course from their plan to encrypt the iCloud backups, due to not wanting to deal with the anticipated backlash from the public, law enforcement and other government agencies/officials. New Fiber Optic Breakthrough Could Surpass 5G, Help Wire Rural Areas  In early January, 2020, the Moscow Institute of Physics and Technology announced that they successfully transmitted data over high-tech fiber optic cables 323 miles (520 Km) at speed over 200 GiB per second, according to an article at Inverse. This throughput rate is faster than 5G, and may represent a better way to deliver high speed internet access to sparsely populated areas, provided that costs are reasonable. The team worked with Russia-based T8 and United States-based Corning to deliver the super fast data speeds. Corning, best known for developing Gorilla Glass that is used extensively in many of today's smartphones, developed the commercial cables used in the feat. The breakthrough has the potential to support up to 400 GiB per second. The initial speed test was limited to 284 GiB per second to insure that the data could be transmitted over the vast distance. The T8 team has its goals set on achieving a throughput rate of 600 GiB per second, using the new system. It is hoping to set a new transmission distance record by sometime next year. Paris Museums Release Over 150,000 Images Of Artwork Into Public Domain  Portrait of Voltaire at the Bastille composing the Henriade, by Louis-François Charon, 1822, from the Musée Carnavalet, Histoire de Paris Paris Musées, a collection of 14 museums in Paris, released more than 150,000 high quality digital copies of works of art into the public domain. They are now available online for you to view, enjoy, and use without restrictions. At the website, you can browse the collection, view images, share images, and even download images of your favorite artwork. On the catalog page of the images, hover your mouse over the catalog entry, and select the "See" button. A new page will open with an enlarged view of the image. Below the image, you should see a "Download" button. Each image you download comes in a ZIP archive file. It will contain at least one high resolution image of the artwork, plus a PDF and TXT file containing information about the image downloaded. Be forewarned ... the archive file downloads can be quite large. The package that contained the image used above had two high resolution copies of the artwork, plus the PDF and TXT files, and came in at over 34 MiB in filesize. So, if storage space is an issue for you, you might want to be a bit selective of which ones you download. In my brief browsing through the catalog, I saw paintings, photographs, drawings, sketches, carvings and castings represented among the selections. From a press release (PDF) from the Paris Musées: The launch of Open Content will mark a new stage in Paris Musées' digitisation policy. It will contribute to enhancing and improving the way our collections are made available and will strengthen the measures taken to ensure better public access to art and culture as well as increasing visibility and understanding of the works in our municipal collections. Making this data available guarantees that our digital files can be freely accessed and reused by anyone or everyone, without any technical, legal or financial restraints, whether for commercial use or not. Digital files that contain works that belong in the public sphere under a CCØ (Creative Commons Zero) licence will be made available to everyone via the Paris Musées' Collections portal. At first only reproductions of works in 2D that are not copyright restricted will be available as Open Content, those works that are still in copyright will be in low definition in order to illustrate, on the Internet site, what is available in the collections. Art lovers will now be able to download works by the great names in photography (Atget, Blancard, Marville, Carjat) or in painting (Courbet, Delacroix, Rembrandt, Van Dyck). This release of new digitized artwork brings the Paris Musées number of artworks offered online to over 320,000 pieces. Hacker Publishes List Of Telnet Passwords For Over 500,000 Servers, Home Routers, IoT Devices  In mid January 2020, a hacker published a list of Telnet passwords for over 515,000 servers, home routers and IoT devices on a popular hacking forum, according to an article on ZDNet. The list includes each device's IP address, username, and the Telnet password. The Telnet protocol can be utilized to take control of internet-connected devices. That IoT devices were included is no surprise. We've covered IoT security issues before. I said it then, and I'll say it again. IoT should be renamed "IdioT" devices, for their gross lack of security features that make them extremely vulnerable to hackers. To those with even a mild concern for privacy and security, you'd have to be an idiot to use such devices. Makers of IoT devices have never heard the maxim "just because you can, doesn't mean that you should." After all, do you REALLY need your refrigerator connected to the internet? If you can't think of another way to compile your grocery shopping list, then compiling that shopping list was never that big of a concern for you in the first place. The hacker compiled his list by scanning the internet and looking for devices that were exposing their Telnet port. The username and password fields were either gleaned from known default usernames and passwords, or by guessing commonly used "custom" passwords. According to ZDNet, all of the data in the list that was leaked was from October and November 2019. It's unclear how much of the list remains current, as devices may have changed IP addresses and/or passwords. ZDNet did not try to connect to any of the devices on the list, since that would have been illegal. PCLinuxOS Magazine News Roundup  In the words of Gomer Pyle, USMC ... Surprise! Surprise! Surprise! Google has killed off yet another service, according to an article on The Verge. This time, they are killing off the PDF-based replica magazines in Google News, where users had to pinch and drag around a page on a phone or tablet just to read the articles. Actually, they quietly killed off two more services in December 2019 as well. Google Hangouts and Google Cloud Print have also bit the dust in the December wave of Google housecleaning. You can view all of the Google Kill List at the Killed By Google website, which keeps track of all of Google's services that have been killed off by the tech giant. Laptop security is a huge deal. Let's say you're working on a project while waiting for your flight at the airport, or you are using your laptop to play a movie to pass the time. What happens if your laptop is suddenly stolen from you? You could pray that you are able to call your bank and secure your accounts ... before the thief robs you penniless. If it's a corporate computer, you could pray that they don't wreak havoc on your corporate accounts before IT is able to sequester your laptop from their servers. But one enterprising user has come up with his own solution. It's called BUS Kill, and you can build your own here, using the plans he has shared with the world. Essentially, it's a dead-man's kill switch. It uses udev commands to lock, shut down or wipe your computer in the event that your laptop is used without the proper USB device connected. It connects to the laptop's USB-A port (there are also plans for USB-C ports, as well, if your laptop lacks USB-A ports), and is held there with a magnetic breakaway USB adapter. The other end is attached to the USB device via a one meter cord that is attached to the user via a small carabiner. The price to build your own will run around $20 (U.S.) for the USB-A version, and around $50 for the USB-C version. ZDNet reported that MalwareBytes has discovered unremovable malware on low end Unimax U673C handsets sold by Assurance Wireless, a division of Virgin Mobile, in the U.S. The handsets are primarily sold to low income Americans through Lifeline, a government-subsidized program to provide phone service to low income users. The handsets are manufactured in China, and the malware has its origins there, as well. Specifically, one installs programs without user interaction, whether the end user wanted them or not. The other one acts as a dropper for second-stage malware, namely a malware package called HiddenAds, which users report having suddenly appeared on their phones. Phoronix reports that Multipath TCP should start coming to Linux with kernel 5.6 laying the prerequisite groundwork. Full Multipath TCP could be coming to Linux as early as with kernel 5.7. Multipath TCP could allow for greater throughput and stability for network connections. The MacOS was the first to fully support Multipath TCP. The Hackaday website reported that one user has added additional LEDs to his USB drive to help protect against rogue USB-based malware attacks. By adding an additional LED (most USB drive enclosures already have one LED), it allows users to distinguish between reads and writes from the USB drive. The Interesting Engineering website reports that an interdisciplinary team of researchers have discovered that using nano-sized copper compounds in conjunction with chemotherapy eradicated cancer in mice, and helped insure that the cancer stayed away. The nano-sized copper oxide particles were able to target cancer cells (which are sensitive to copper oxide), while leaving healthy cells untouched. There is some suggestion that the addition of nano-sized copper oxide particles might also act like a vaccine, preventing further cancerous growth or progression. On a Google blog post, Google reported that it plans to end support for third-party cookies within two years in Google Chrome. Third-party cookies typically allow ad owners to track you across the web to see how their ads are performing. Hurray! Hurray! Hurray! Finally, Google is doing something for user privacy! I doubt, though, that they would have done so without an ever-increasing public outcry for increased privacy across the web. If you are a Google Maps user, it has saved every trip you have ever made (especially on your mobile device). The CNBC website has an excellent article on how to stop Google Maps from tracking you and saving your location history. The level of detail is c-r-e-e-p-y. Like when you leave work, any stops you make on your way home, when you leave for work, what pictures you took where, and whether you were walking, driving, riding on a train, or bicycling. With its default settings, Google sucks up all of this data ... and retains it FOREVER! That is, unless you go in and make the changes that the article suggests. Honestly, I was shocked at not only the level of detail that Google Maps Hoovered up about my trips, but also how far back it went. |







