| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Mind Your Step, Part 2 |
|
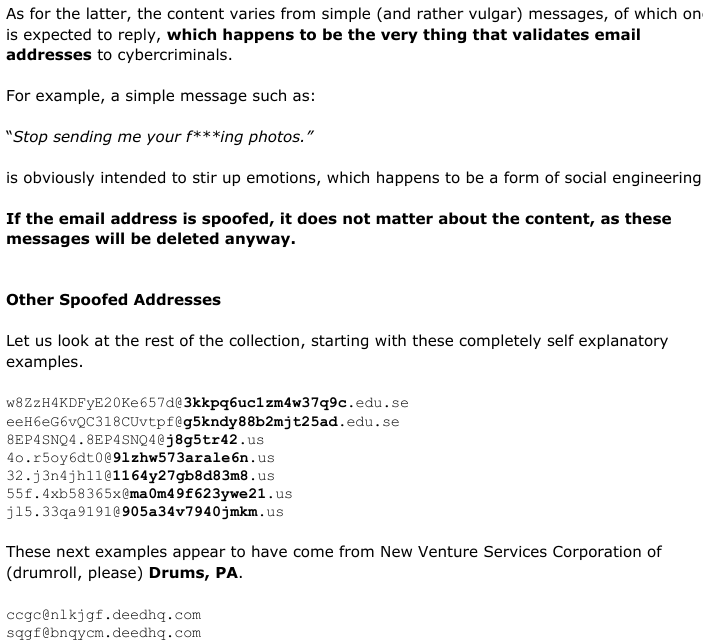
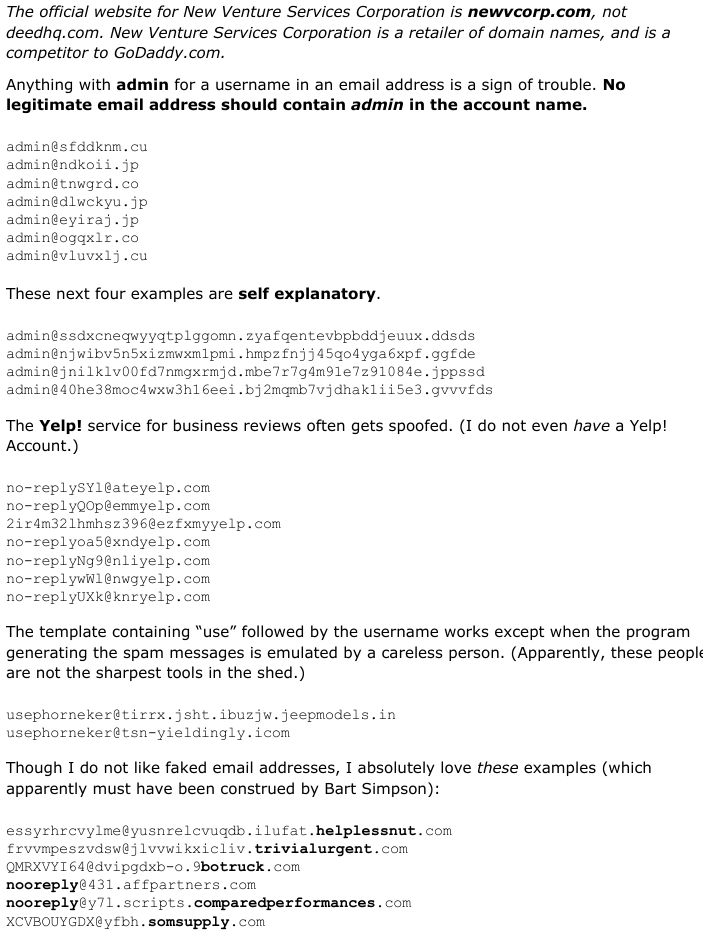
by phorneker This is the second installment of this new series. At the end of the last issue, I had discussed fake email addresses. This past month I collected a series of fake addresses used as the apparent sender of a series of fake emails. Mail handler applications such as SpamAssassin determine what is a legitimate email and what is a fake email by examining the header information contained in the email. There are two mechanisms that are used to be sure that what gets sent out from your email account really did come from your email account. The first is the Sender Policy Framework, which is configured at the domain servers where your domain is hosted (such as GoDaddy). The second is the DomainKeys Identified Mail standard (http://www.dkim.org) for authenticating the sender of emails. G-Mail already has this mechanism implemented. So how does an email with a fake sender address get through in the first place? The answer to that has to do with the Simple Mail Transport Protocol, or SMTP for short. SMTP was designed to get email sent out as quickly and as simply as possible. These days, that is exactly what is wrong with SMTP as a means of sending out emails, especially at a time when we have to worry about identity theft (and its long term consequences).  So, what goes on behind the scenes when an email is sent? First, the email client connects to an outgoing SMTP server, then issues an EHLO command to get that server's attention. The outgoing SMTP server then asks for the SMTP username and password. The email client responds appropriately. It is here where the spoofing of the sender's email address is possible. The email client issues a MAIL FROM: sender identifier <email address> where sender identifier is the name associated with the email address enclosed in <>. Next, the email client receives a 250 code meaning “all is well” for the outgoing SMTP server. Then, the email client issues a SEND TO: receiver identifier <email address> where the parameters are for the receiver instead of for the sender. The main problem here is that the outgoing SMTP server does not check to see if either address is valid or even if either address is legitimate. Hence, the aforementioned mechanisms, SPF and DKIM are necessary additions to the outgoing SMTP server so that the server can check for authentication of email addresses before the email can be accepted for delivery. The other part of the problem is that the SMTP client is not necessarily going to be Thunderbird or Claws, or even a web browser. It could be a customized spam generation program written in C++, Java, Python or Ruby. Email Spoofing vs Email Hacking The fake sender email addresses I collected were the result of email spoofing. email spoofing is to electronic mail what robocalls are to landline and cellular phone service. The main goal of email spoofing could well be nothing more than to validate your email address to cybercriminals, or could be an attempt to gain vital information needed to steal money, or worse, your identity. email hacking, however, is a much more serious problem. This means that a cybercriminal somehow gained full access to your email account. (If this happens, it is a good idea to at least change the password, or better yet, close the email account outright.) This is one reason why everyone should change his/her password on all essential and valuable accounts often (such as your Google account) and make those passwords as difficult to guess as possible. Also, make sure that two factor authentication is enabled wherever and everywhere possible. Hillary Clinton Sure Had The Right Idea... So what do we do with emails containing spoofed email addresses (especially those in the Spam folder)? Delete them, of course. By deleting them, your email address will never be validated, no matter how often the spam machine is used....and if worse comes to worst, simply close the email account and open a new email account elsewhere. The cybercriminals will eventually get the message. If You Must Close Your Email Account... Before you decide to close your account, it is a very good idea to contact those people (and businesses) who legitimately have your email address and inform them of the change of email address. Types Of Fake Email Addresses The most common type of fake email address can be replicated with a simple function in Ruby. 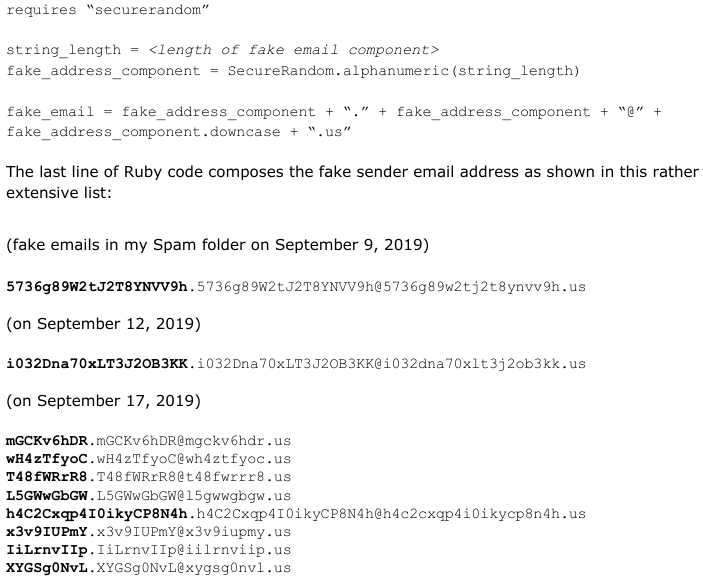  
|