| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
SplashData's 100 Worst Passwords Of 2017 |
|
by Paul Arnote (parnote)
On December 19, 2017, SplashData released its list of the 100 worst passwords of 2017. People never seem to learn, since there are many perennial favorites on this list. SplashData, who sells password management software, has compiled the list of poor passwords since 2010. The data is gleaned from information gathered from the many data breaches of personal information that occurred over the past year. So, before we talk about much else, here is the list. Among the first 25 passwords, a number after the password represents the number of positions of change from the 2016 worst password list. If a password is new to the list, it will be denoted as "new" instead of a number. Similarly, passwords in the list that haven't changed positions from 2016 will be denoted as "unchanged." If a password you use is in this list below, you might want to consider changing it. You obviously weren't as original as you should be. Editor's Note: Some of the passwords are what many would call profanity, so the list shouldn't be considered "family friendly." However, they are included here for the sake of completeness and factual reporting. For the naughty words in the list, highlight the text after the number to see the word.
1. 123456 (unchanged) Of course, the perennial favorites still top the list, where they've stayed for some time. Both "123456" and "password" have been at or near the top of the list ever since the list has been compiled. Passwords related to sports ("soccer" or "football") or favorite sports teams ("lakers" or "rangers" or "yankees") remain popular. This year, probably because of the new Star Wars movies coming out to a whole new generation of Star Wars fans, "starwars" as a password cracks the top 20 worst passwords. The "rage against the machine" is evident, with passwords such as "letmein" and "biteme". The rising political division is also evident, with such passwords as "trustno1" and "freedom". Still popular are keyboard patterns, such as the "1qaz2wsx" and "qwerty" passwords. Best Practice: What Makes A Good Password In years past, we thought this was an easy one to answer. But in August, 2017, Bill Burr set the password world on its ear. See, Bill Burr was the employee of the National Institute of Standards and Technology who released a report in 2003 advocating for the use of special characters, mixed case letters, and numbers in a password in the hopes of fooling/foiling hackers. Literally overnight, his paper became password policy. It became the FINAL WORD on passwords. (Read the full USA Today article here.) But in August, Bill Burr stated in a Wall Street Journal article, "Much of what I did, I regret." His report wasn't based on any real-world password experience or expertise. Rather, it was based on another paper written in the 1980s. But in the interim, it became entrenched as THE holy password gospel. Bill Burr now suggests that users string together four common and random words, instead of the "standard" mix of uppercase and lowercase letters, numbers, and special characters. The XKCD comic shown here sums up nicely why and how this is better. 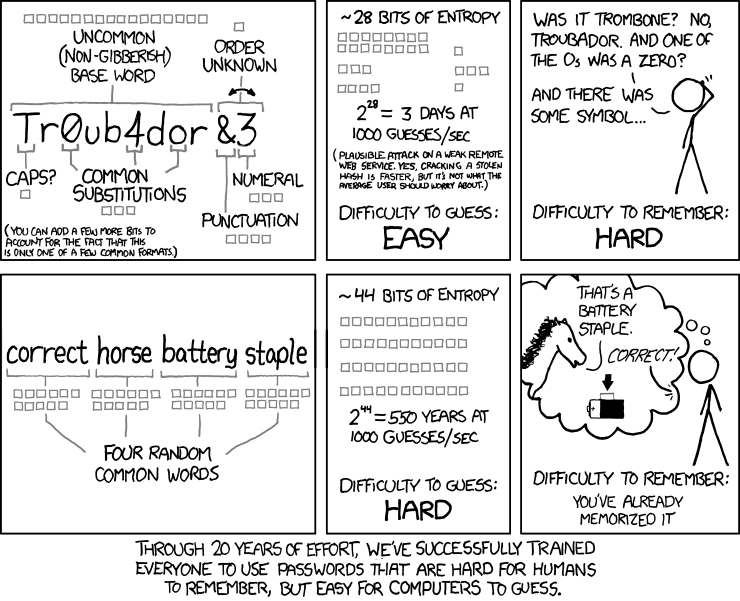 But don't expect to see websites and other entities jump aboard with this new revelation, as many of them will still require the "standard" mix from that 2003 report that has become password gospel. Those "recommendations" are firmly entrenched in the password world as key tenets of the "religion." After all, it took us nearly 20 years to get to that point, and it's likely to take twice as long (or more) for those erroneous thoughts to erode, despite evidence that there is a better way. So many bad ideas take so long to go away. Still, it's apparent that many users are sloppy with passwords. This is evident from the 2017 Worst Passwords list. So, there are ways to help protect yourself with strong passwords. The fact remains that there is no uncrackable password, given enough time. But the goal is to make it sufficiently difficult to crack that the hackers will simply give up and move on to the next poor sucker in line, leaving your data safe. Who knows? Maybe the next poor sucker has a password that is on this worst password list. Use a password manager. What to use depends on whether you trust the cloud or not, and what level of convenience you are seeking. If you want to use the same password manager on several devices (and who doesn't use multiple devices these days), then a cloud based solution is what you need. Probably the premiere service is LastPass, a web browser plugin. It will remember all of your passwords for your websites that require them, and help generate secure random passwords for new websites. All you have to remember is your "master" password. Don't get amnesia, because if you forget your "master" password, even the folks at LastPass can't retrieve your passwords without it. They most likely can't/won't be able to retrieve your passwords WITH your master password, either. If a local, non-cloud solution is more to your liking, you can install KeepassX, which is in the PCLinuxOS repository. It works much like LastPass, but without the cloud part. Your passwords are saved in an encrypted file on your hard drive. There are other password managers out there. So, if either of these aren't necessarily what you're looking for, give one of the others a try. Just be careful about where you place your trust. Don't use the same password on multiple websites. This should be a no-brainer, but it happens all the time, many times a day, all over the world. First, humans are creatures of habit. Second, it's much "easier" to remember one or two passwords that you use all over the web. Of course, easier for you also grants easier access to your personal data – for the hackers (if I have to explain this, then you really haven't given the security of your data much thought at all). If the hackers get ahold of one of your passwords, they will attempt to use it at other sites. Make your passwords unique for each site (which makes using the aforementioned password manager even sweeter and more desirable). Avoid pop culture and personal "treasures." Pop culture words, like your favorite sport, sport team, movie, movie character, actor/actress, etc., will always be popular choices when you're trying to pick a password that reflects your tastes and "inner you." Avoid them, because you're likely not the only fan who has chosen to use that pop culture word or phrase. If you were, it wouldn't be pop culture. Similarly, avoid personal "treasures." This means avoid using birth dates, wedding dates, anniversary dates, address, names of children, names of pets, names of favorite foods, and anything else that is either common knowledge or easily ascertained knowledge about you. Summary It does seem that data breaches are occurring at an ever increasing rate. In fact, data breaches are becoming all too common. This is understandable, since YOUR personal data is the currency d'jour for hackers and other unscrupulous folk, as well as various governments around the world. Some of the more common companies that experienced data breaches just in 2017 include Verizon, Saks Fifth Avenue, Deloitte, and Uber. Let's not forget about the huge Equifax breach that exposed the personal information of millions of people. The statistics concerning data breaches don't include the perennial sieve called Yahoo!, or adult websites. YOU are the only person who actually cares enough about your data to keep it protected. Despite their attempts to convince you otherwise, companies true loyalty is to their bottom line and their stockholders. That protection of your personal data should – and does – start and stop with YOU. If you're sloppy with your passwords (weak, ineffective passwords, reused everywhere), you will eventually reap what you sow. You likely will not like the bitter crop that results. |






