| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
10 (Potentially) Fatal Linux System Security Sins |
|
by Paul Arnote (parnote) Let's face it. Those of us that use Linux, do so because we like it. We like that it is free, as in beer. We like that it is robust. We like that we have many more choices under Linux. We like that it is secure. We like that it is virtually virus free. We like the community that has built up along side of Linux. There's a lot to like about Linux. But, are YOU doing something that potentially destroys that sense of security you get from running Linux, maybe without even realizing it? Be careful, or that utopian Linux world may come crashing down around you. Let's look at ten of those actions that can make using Linux a literal nightmare. 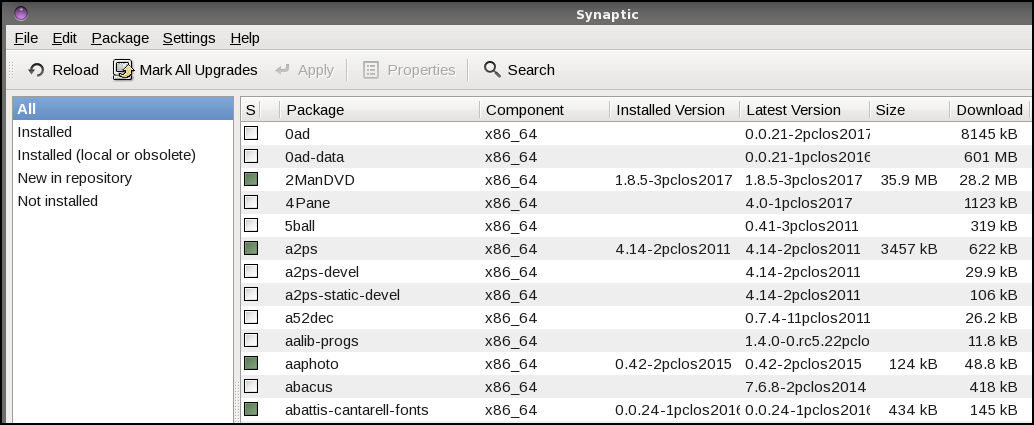 #1. Installing from outside the official repos. If you've spent any significant amount of time using Linux, you most likely have committed this cardinal sin. The Widgetery program that you need just isn't available in the official repos, and there isn't broad enough interest in it amongst the community for the maintainers to add it to the repos. However, you've located the source files. You take it upon yourself to compile and install the Widgetery program and some of its dependencies yourself, from the source files. Initially, things are likely to run just fine. But let's say six months down the road, another program that has similar dependencies to Widgetery is added to the repos, and you install it. The newer program updates some of the lib files that Widgetery relies on, breaking Widgetery because it hasn't been updated to use the new lib files. Widgetery now refuses to run properly. Thinking that the problem is with Widgetery, you reinstall Widgetery and its dependencies from source. Now, the new program refuses to run, because the newer versions of the lib files that it needs are no longer there, having been replaced with the versions that Widgetery needs to run properly. This is known as "dependency hell," and represents an oversimplified example. Often times, this incompatibility goes on for multiple layers of dependencies, making it impossible for all but a well seasoned maintainer to resolve. When a package is added to the official repos, great care has been undertaken by the repo maintainer (generally) to insure that when a new package is added and installed, it doesn't "break" other programs. Anyone can build and compile a program from source with a minimum of effort. But it takes some significant knowledge of the overall picture of the other programs that are in the repos to insure that everything runs well together. That's knowledge that most of us do not possess, and it's knowledge that takes quite a bit of time to acquire. You can experience similar catastrophes by installing packages intended for one Linux distro on a different distro, since the maintainer of the other distro might have packaged things just a little bit differently than the maintainer of your distro. Another potential pitfall you can experience from installing programs from outside the official repos is that you might unwittingly and unknowingly install malicious software. That malicious software may put your data and sensitive information at risk. You have to do quite a bit of research to be certain that the programs you are installing aren't going to compromise your data or sensitive information. Once installed, that malicious software now potentially has access to your entire system, including your files, email contacts, emails, browser history ... everything! In short, it's rarely worth the risk to install programs from outside the repos. PCLinuxOS has a policy of NOT providing support for your installation if you have installed software from outside of the official PCLinuxOS repository. Quite simply, no one really knows exactly what changes were made to your system. If you ever wondered why this seemingly onerous rule exists, you now know why. #2. Not updating regularly. Distros, like PCLinuxOS, are constantly being updated. Failure to update your system regularly is a very unhealthy habit. You expose your system to security issues and vulnerabilities by not having the latest software installed. Updating your software allows you to stay one or two steps ahead of new exploits. Plus, updates often include new features and improved stability. Linux doesn't remain the stable, secure platform it is by remaining stagnant. As security vulnerabilities and exploits are discovered and closed, so should your operating system and programs be updated to protect against those vulnerabilities and exploits. As technology changes and moves forward, so should your operating system and programs. As programs evolve to better meet the needs of the user, so should your operating system and programs. The only way to keep pace is to keep your system updated with the latest versions available in the software repository. #3. Selectively updating. This is a sure fire way for failure. It won't strike you right this minute were you to selectively update, but it will eventually catch up with you. Updating only the few programs you regularly use, but none of the rest of your system, can cause broken dependencies and cause programs to no longer function properly. You should only ever update your entire system. In Synaptic, you do this by selecting "Mark All Updates," and then "Apply."  #4. Weak root password. You wouldn't leave the key to your house or car just sitting there in the lock, would you? Just like the keys to your house or car, the root password is the key to gain access to your Linux installation. Don't make your root password easy to crack by protecting your system with a weak root password. Yes, knowledgeable people can change your root password to anything they want, if they know how. But the vast majority of users don't know how to do it, or don't know that is even possible. #5. Ignore your kernel. Just running updates isn't enough. Regular updates won't update your kernel. That is something you have to go in and do manually. Running on an outdated kernel can expose your computer to security vulnerabilities and exploits. Older kernels also will not offer the level of hardware support that newer kernels offer. Keep just one kernel that works on your computer, plus the latest kernel. You don't have to keep eight different kernels installed on your computer. There is no benefit, and it just takes up precious drive space. Let's say you have been using 4.11.4 and 4.11.6 comes out. You can remove version 4.11.3 of the kernel, keeping 4.11.4 as your "backup" kernel. #6. Avoid the command line. It's easy to understand why some people shun the command line like they shun a major illness. Today's Linux desktops are stable and robust. They are easy to use. But what happens when your computer won't boot to a GUI desktop? You don't have to be a command line commando, but you should at least know a handful of command line commands, should you ever be forced to use the command line. Plus, who knows ... you may discover that you actually LIKE the command line. Some things are much easier to accomplish there than through a GUI. You might also discover that things happen there much faster, are more reliable, and offer more security.  #7. Don't backup important system/configuration files. Face it. Until something else comes along to replace it, we're pretty much stuck with Xorg. Wayland has often been touted as Xorg's replacement, but even that seems to be way off on the horizon. So, until either Wayland or something else that hasn't gained prominence yet appears, we'll be using Xorg. If you've used Linux long enough, you are familiar with the situation where Xorg is updated, but something in the update process didn't go exactly as intended. When you reboot, you find yourself unable to launch the X server. If you see that Xorg is going to be updated, make a copy of your working xorg.conf file (located at /etc/X11/xorg.conf) in the /root directory. That way, if something goes awry, you have your backup handy to be restored from the command line. The same thing goes with Apache, Samba, MySQL and any other critical system files you might need. #8. Misunderstanding permissions. Part of the security of Linux is that some files are protected from standard users. That is, regular users don't have permission to edit certain files. While this can be somewhat inconvenient if you are the administrator of the computer, but logged in as a regular user (which you should be ... more on that later), avoid changing the permissions on the file in question. It would be tempting to simply change the permissions by issuing the command chmod 777 at a command line prompt. But, that would be risky, since that gives read, write and execute properties to ALL users ... even malicious users. So, here's a fairly easy way to understand user permissions:
777 read, write and execute permissions for all users Of course, it can get a bit more complicated than this, but this abbreviated table should give you some basic understanding of how permissions work. The last thing you want to do is give unfettered access to things that others should have no access to. #9. Logging in as the root user. Never, ever, ever log in as the root user. If there are some tasks that you need to complete as the root user, su to root, complete your work, and then go back to a regular user. When you login as root, you have access to -- literally -- everything. It will also allow any malicious users or software the opportunity to carry out their malicious deeds. Plus, if you make a mistake (delete the wrong file, for example), it can be catastrophic for your system. 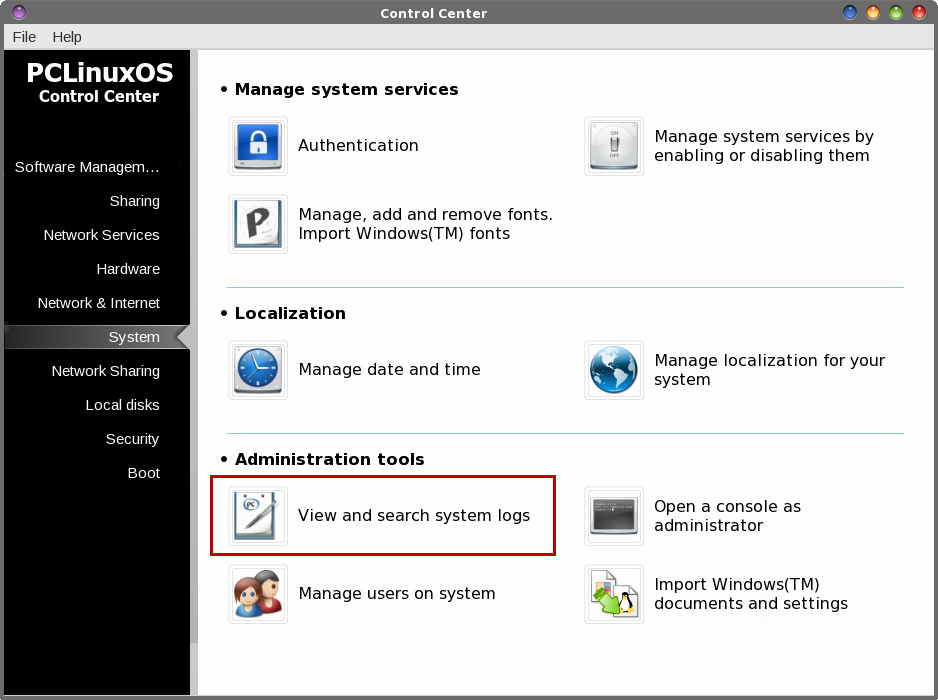 #10. Ignore log files. I suspect most Linux users are guilty of this. I know I don't pay as close attention to my system's log files as I probably should. Fortunately, Linux stores most of its log files in one convenient location: /var/log. Your log files will help you figure out any problems you might be having with your system. Those problems could include hardware problems, hardware recognition, system services that are failing to load, etc. If you're suspecting security issues, check in /var/log/security. Otherwise, /var/log/messages should be your first place to look. This is a common log file where all generic errors and messages are logged. It should contain information about networking, media changes, etc. The best and most complete way to view your log files is directly in a standard text editor. PCLinuxOS users have another choice, though. You can search through your system log files by opening the PCLinuxOS Control Center (PCC), and going to the "System" tab. There, under the "Administration tools" section, you can select "View and search system logs," highlighted with the red box in the image above. PCLinuxOS users can also install logcheck and logwatch via Synaptic, for two other options for monitoring log files. Summary One of the things we all love about Linux is its security. The last thing you will want to do is compromise that security with poor security habits. I'm not going to say that you will be exempt from any issues if you follow all of these practices, but I will say that you will have a much more secure system. In today's environment where there's a security risk to your computer and your data/information behind every blade of grass, you can't be too careful. You'd hate to open the doors wide to the kingdom, when keeping them closed and everything secure is so relatively easy. |


