| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Weak Password? Five Ways To Generate Strong Passwords |
|
by Paul Arnote (parnote) We've written about passwords and security several times within the pages of this magazine. We've shown you ways to generate secure passwords. We've talked about how a secure password can protect your data, both online and on your physical computer. Yet, all too often, and despite all that they have heard and learned about password security, users still lean towards employing the weakest of passwords. Much of the time, users tend to use the same password on most (if not all) of the sites that they regularly sign into. Sure, it's easier to remember one password (complex or simple) than a dedicated password for each site.  Enigma Machine at the Imperial War Museum, London. (Public Domain) We're not going to rehash our previous articles here on password security, and why it's important. If you didn't listen the first time, chances are good that you won't listen the second, third, tenth or hundredth time, either. At least, not until you become a victim of an insecure password. Users who take password security seriously are often viewed as paranoid, if nothing else. At least, until you become a victim of an insecure password. Everything we've written previously about choosing and using a secure password, still applies. Everything we've written previously about using a "base password" that is modified for each site you log into, still applies. Everything we've written previously about the foolishness of reusing passwords, still applies. Everything we've written previously about using a password manager (such as KeePassX or LastPass), still applies. Rather, this article will showcase some tools you can use to help generate unique and secure passwords. How you use them is entirely up to you. Remember that longer, more complex passwords offer more security than passwords that are short and made up of everyday words. Use of numbers, symbols and punctuation increase security. Lastly, you should take the time to test your password (or one similar to it with the same length and similar complexity, if you're truly paranoid) on a site like "How Secure Is My Password?". It will serve as confirmation that you have given due diligence to creating secure passwords, but keep in mind that it is anything but a guarantee of security. The best you can do is slow down a hacker to such a point that they will skip over your data and move on to less secure data that is easier pickings. Enigma If that small, six letter word conjures up visions of the losing side of World War II, you would be on the right path. Its place in the cryptologic Hall of Fame is guaranteed for all time. Given how much time, man hours and energy were placed into breaking the Enigma encryption, why not consider using it to create a secure password? The process is/was solid. What eventually led to the breaking of the Enigma code was its sloppy implementation by its users. Their sloppiness and laziness contributed to the codebreakers at Bletchley Park and elsewhere to more rapidly breaking the code. You can read more about the Enigma cipher machine here. 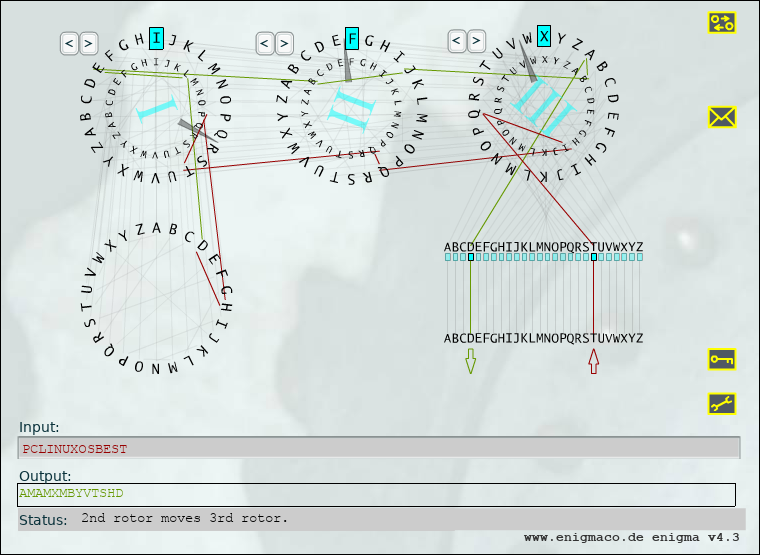 Today, a real, working Enigma machine is hard to come by. But thanks to an online simulator, we can all get a pretty accurate feel for how Enigma worked. In the image above, we put in the phrase PCLINUXOSBEST, and get AMAMXMBYVTSHD back as the encoded output. Granted, the output isn't necessarily the easiest to remember, but if you're using a password manager, you won't necessarily have to remember it (but I wouldn't put all of my eggs in the password manager egg basket … I'd have a backup copy saved somewhere safe). For what it's worth, because of the pseudo-randomness of Enigma and how it works, you will most likely get a completely different output than I got in the example above. OpenSSL This program is included in the base installation of most versions of PCLinuxOS. If you find it missing, install it from Synaptic. Don't shy away from it just because it is a command line program. It's quite easy to use. openssl rand 14 -base64 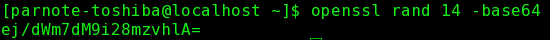 The rand parameter evokes the pseudo-random generator, while 14 tells it how many bytes of data to create. The -base64 option insures that the result can be typed from a keyboard. IT professionals typically cite a minimum password length of 14 characters to be ideal, since a password of that length -- utilizing uppercase and lowercase letters, numbers, symbols, and punctuation -- will require enormous computing power to crack via brute force methods. This is why we use the 14 in the command above. Of course, you can use any number you want. Looking at the output, you will realize that we have produced 19 characters. You can use the output as is, or you can truncate or edit the result to give you just 14 characters. The choice is entirely up to you. Just keep in mind that longer, more complex passwords are typically stronger, harder to crack, and thus more secure. pwgen This program is installable on PCLinuxOS, via Synaptic. It's job is to produce secure passwords that can be easily remembered by humans. Again, this is a command line program, but don't let that deter you or scare you off. It, too, is very easy to use. pwgen 14 1 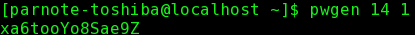 The 14 specifies how many characters long to make the password. The 1 tells pwgen to make only one password. Change the 1 to any other number and pwgen will create that many passwords. 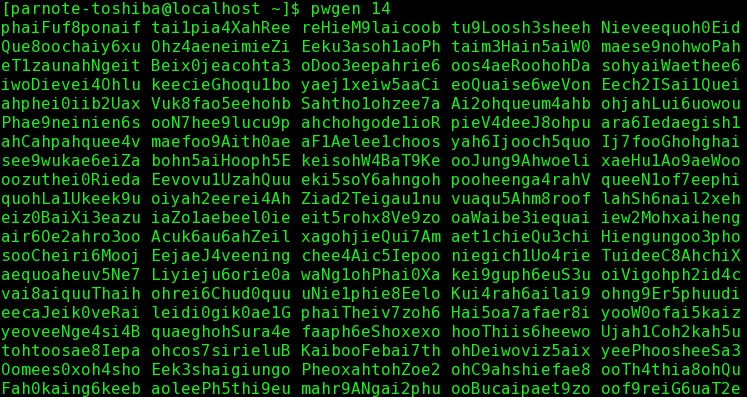 If you omit the last number telling pwgen how many passwords to generate, it will default to providing you with 100 passwords to choose from, all 14 characters long. Of course, if you want longer or shorter passwords, simply replace the 14 in the command with the length of characters you want for your password. You will notice that each password generated by pwgen is exactly the number of characters you specify. gpg, or Gnu PG, or Gnu Privacy Guard Whichever name you prefer to use, they all relate back to the very same program. Gpg is typically thought of to secure the contents of files and email, something it excels at. But you can also leverage gpg to create secure passwords. Again, don't shy away from using this powerful command line program. Gpg is installed by default in most PCLinuxOS installations. If you find it missing, install it from Synaptic. gpg --gen-random --armor 1 14 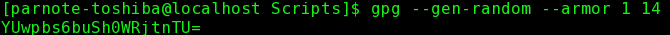 Similar to openssl, even though we specified 14 characters (or bytes) as the length of the password to generate, gpg provided us with a 20 character password. Use Perl Perl should be installed by default on your copy of PCLinuxOS. If it is not, install it from Synaptic. If you're not familiar with Perl, it is a programming language that is a lot like bash scripting, with a twist of C. Enter the following into your favorite text editor, and save it somewhere in your /home directory as password.pl.
#!/usr/bin/perl Then, move to the directory where you saved the script, and enter the following: perl password.pl 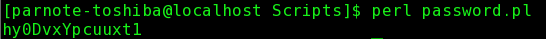 You should see something like what's depicted in the screen capture above, on your screen. Notice the "0..13;" at the end of the third line of the script. This is where we set the length of the password that is generated. With this script as presented, it produces a 14 character random password. But, if you want a 20 character password to be generated, change the "13" at the end of the line to "19." Because Perl uses a zero based counting system (that is, it starts counting at zero, instead of one), always subtract one from the number of characters you want. You can change this number to any number you like, so you can also make shorter passwords (although I can't imagine why you'd want to do that, from a security standpoint). Summary So, there you have it. Five ways to generate unique, secure passwords under Linux. You owe it to yourself to follow the established recommendations of not only using a secure password, but to also avoid reuse of passwords between sites. Data, or rather access to data, has become the currency of criminals around the world. Once they have your data, life can get pretty difficult and troublesome. Keep your data -- and yourself, ultimately -- safe from those who would like to get access to it, but who have no rightful purpose to access your data. |

