| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Encrypt VirtualBox Virtual Machines |
|
by Paul Arnote (parnote) One of the newer features in VirtualBox (starting with version 5.x) adds the ability to encrypt your the virtual hard drives of your virtual machines. In today's computing environment, where your privacy is always under attack from all sides, you may find it necessary to apply encryption to your VirtualBox VMs. Don't be so quick to dismiss the need for encryption. For example, here in the U.S., many of us use (and buy) income tax software every year to fill out and submit our income taxes. Contained within those files are some VERY sensitive and private data that could lead to devastating ruination should it ever fall into the wrong hands. Unfortunately, unless you use online services to fill out and submit your income taxes (which have a whole other set of security issues), all of the tax software runs either on Windows, OS-X, iOS or Android. There is nothing that will run natively on Linux. As such, the omission of tax software that runs natively under Linux pushes Linux users to often run their chosen tax software in a virtual machine, usually VirtualBox. That is but one example of private, personal, sensitive data that you don't want falling into unscrupulous hands. I'm sure that you can think of other sensitive data pools that are relevant to your use. Being able to encrypt your VirtualBox VMs will help insure that your sensitive data doesn't fall into the wrong hands. Gettin' 'Er Done To start off, you have to have your VM already installed. The VM also has to be powered down. You cannot perform the encryption on a VM that is paused or in a "snapshot" state. 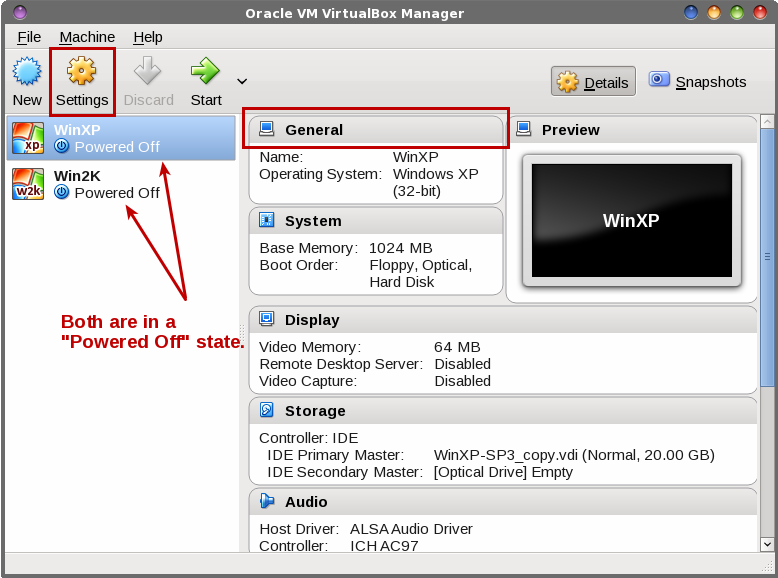 Next, you need to select the VM you want to encrypt. Be sure that the VM says "Powered Off" as the state of the VM. If it doesn't, then start the VM and properly power it off. Then, click either on the "Settings" icon on the toolbar, or on the "General" heading near the center top of the window (outlined in red in the image above). 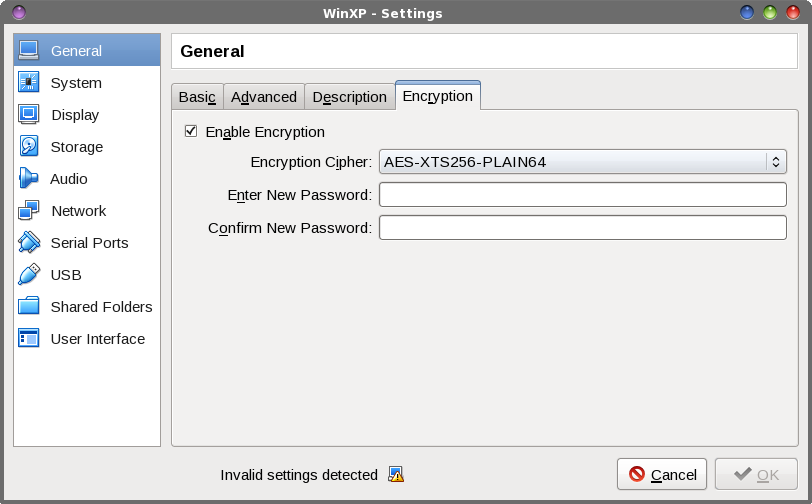 Now, place a checkmark next to "Enable Encryption," and choose which level of encryption you want to use. Your choices are either AES-XTS256-PLAIN64 (shown) or AES-XT5128-PLAIN64. The difference is whether you use 128 bit or 256 bit encryption. The third (and default) choice, "Leave Unchanged," doesn't seem like the smartest choice. As I'm writing this, I cannot wrap my head around why you might want to use this particular choice. Just as you should be doing with all of your passwords, choose a strong password using a mix of upper and lowercase letters, numbers, symbols and punctuation marks. Be forewarned: someone out there has already made a tool to crack weak passwords used with VirtualBox's VM encryption. The tool uses a brute force method that will make weak passwords fall like the walls of Jericho, rendering your encryption useless – and potentially exposing your data to prying eyes ... or worse. With that in mind, enter your SECURE password in the first password entry box. Then, re-enter your password in the second password entry box to confirm it. Now, just click the OK button. Once you hit that OK button, go do something. Make a sandwich, or grab a snack. VirtualBox will be encrypting your entire virtual hard drive, so it may take a little bit of time. You might get a bit bored watching and waiting for the progress bar to make its way to 100% completion. Now, whenever you launch your virtual machine, you will be prompted for your VM password whenever you launch it. Summary With your privacy and data under assault from multiple vectors these days, you cannot be too careful with your data. An ounce of prevention is worth more than a pound of cure. But once your data has fallen into the wrong hands, there is no cure. Thus, that ounce of prevention becomes the cure. Protect your data and prevent it from being compromised in the first place. Thankfully, VirtualBox gives you the tools to help protect your data. If you don't use the tools you are provided, then you have no one to blame but yourself for any breaches in security. |





