| Previous
Page |
PCLinuxOS
Magazine |
PCLinuxOS |
Article List |
Disclaimer |
Next Page |
Gain Control Of Firefox "Flash Is Out Of Date" Message |
|
by Paul Arnote (parnote) Adobe Flash. What a scourge on computer users. Thanks to Adobe, the creators of Flash, it remains one of the largest security vulnerabilities on anyone's computer. Horrid tales of code jumble are legendary, so much so that there are reports that the code is impossible for any programmer to follow. Certainly, this adds to Flash's security issues. Couple that with Adobe's steadfast refusal to open source Flash (as if they make any money off of it, anyway), this nefarious plugin has made just about every computer user gain new gray hairs and curse its existence. Most computer users can't wait for the death of Flash, and for it to vanish from the computing landscape. I am among those users. With the arrival of HTML5, Flash's days appear to be numbered, and Adobe will be relegated to -- at best -- a minor, bit player with regards to streaming online content. For me, as well as a lot of other consumers of streaming online content, that day cannot come fast enough or soon enough. So, for the time being, we are stuck with Flash to play certain streaming online content. But the numbers are shrinking for sites and files that require Flash, as HTML5 gains an ever increasing beach head in the war.  It's because of the ever increasing security vulnerabilities of Flash that we have to endure an almost weekly update of the Flash player plugin. It seems like every week, some hacker discovers yet another new way to exploit yet another security hole in Flash. Since Flash is now (essentially) embedded in Google Chrome, every new security vulnerability that is fixed necessitates yet another update of Google Chrome. Since Adobe stopped officially supporting Linux, I'm not too sure from where the Flash player plugin for the Linux version of Firefox actually comes. But show up it does. And frequently. Sure, I could just switch to using Google Chrome as my everyday web browser. But I don't like Google Chrome as well as I like Firefox. I've been a Firefox user ever since it was released, and I've grown comfortable and familiar with how it works. I have a bevy of plugins and extensions that I use with Firefox, and they are integral with how I've come to work with Firefox. Chrome doesn't have the same "feel" for me. It certainly doesn't "feel" like home. Plus, a lot of the plugins and added functionality that I've come to depend on in Firefox just aren't available under Chrome, they don't function the same way, or some of their functionality is lost. 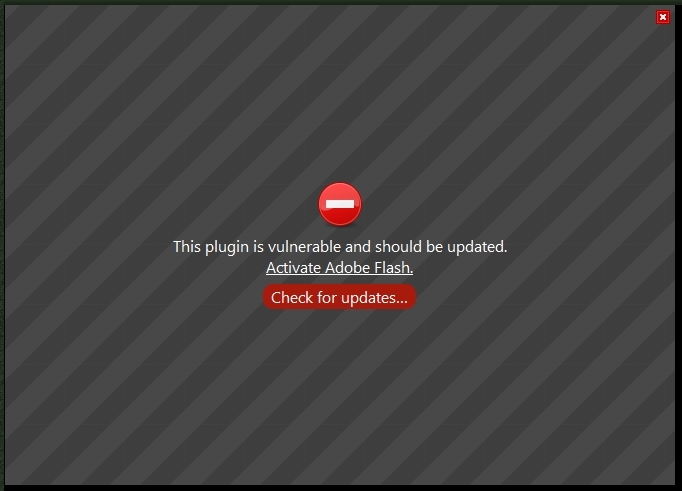 When I see the image above, I know that Flash has been updated ... again. So how does Firefox know to "flag" your version of Flash as vulnerable? The answer lies in some new policies and files that are maintained by Firefox. Starting with version 2.0, Firefox has had settings that allow for the blocking of malicious plugins. Around version 18 or 19, Firefox also added the ability to block vulnerable plugins. By default, Firefox downloads a new "blocklist.xml" file daily. Firefox keeps track of the time by monitoring how many seconds has elapsed since the last daily file update. So, 24 hours equals 86,400 seconds. When 86,400 seconds have elapsed since the last blocklist.xml file download, Firefox downloads a new one. So, that is how Firefox knows whether or not your plugins and extensions are "up to snuff." In the case of Flash, the annoying message above is displayed on every single website you view that uses Flash. You will have to "Allow" the "outdated" plugin to run on every single site that you visit ... and this gets old, fast. Obviously, the ideal solution is to run updates on your copy of PCLinuxOS. But, if you're not in a position where you can run updates at that moment, or if you typically only run updates weekly or bi-weekly, then one of the following solutions may be more to your liking. 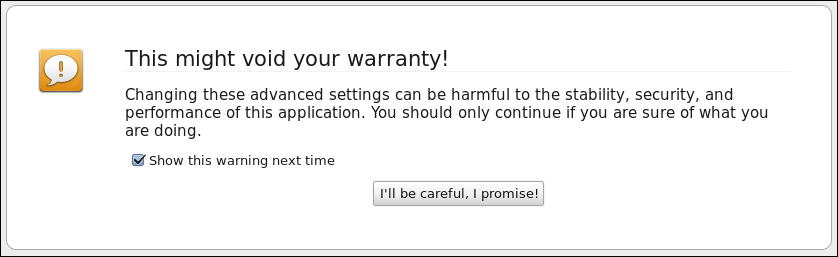 Go ahead and type "about:config" in Firefox's address bar. Click on the "I'll be careful, I promise!" button (and please ... do be careful). Next, type "extensions.block" on the Search line. You should see several entries listed. They are, with the default values in parenthesis: extensions.blocklist.detailsURL(https://www.mozilla.org/%LOCALE%/blocklist/) extensions.blocklist.enabled (true) extensions.blocklist.interval (86400) extensions.blocklist.itemURL (https://blocklist.addons.mozilla.org/%LOCALE%/%APP%/blocked/%blockID%) extensions.blocklist.level (2) extensions.blocklist.pingCountTotal (user set) extensions.blocklistpingCountVersion (user set) extensions.blocklist.url (https://blocklist.addons.mozilla.org/blocklist/3/%APP_ID%/%APP_VERSION%/%PRODUCT%/ %BUILD_ID%/%BUILD_TARGET%/%LOCALE%/%CHANNEL%/%OS_VERSION%/%DISTRIBUTION%/ %DISTRIBUTION_VERSION%/%PING_COUNT%/%TOTAL_PING_COUNT%/%DAYS_SINCE_LAST_PING%/) You *could* just disable the blocklist entirely. You *could* set "extensions.blocklist.enabled" setting to "false," or you could change the "extensions.blocklist.url" setting to "" (or NULL). But I wouldn't recommend doing either. By doing so, you prevent Firefox from blocking not only extensions and plugins with vulnerabilities, but you also prevent Firefox from blocking malicious plugins. In short, you could be inviting all kinds of (in)security issues upon yourself. So, this is probably not the best way to go. You could change how often Firefox downloads the blocklist.xml file. Since the default is 24 hours, or 86,400 seconds, we could change the interval to something longer. Here are some other intervals you might be interested in:
Week (7 days): 604800 Another choice could be to change the blocklist level. The "extensions.blocklist.level" is set to "2" by default, which means to "hardblock" extensions listed in the blocklist.xml file. By "hardblocking" the extensions, they will not be run unless there is user intervention telling Firefox to go ahead and run/use that extension. Changing the level to "1" should change the blocking level to "softblock." This tells Firefox that the item is in the blocklist, but the problem is not severe enough to warrant forcible blocking. Still another choice could be to simply delete the blocklist.xml file from your computer (on my computer, it's located at /home/parnote-toshiba/.mozilla/firefox/pwgl1kmj.default/ blocklist.xml). This is useful only until Firefox downloads another copy when 86,400 seconds is up. Still, it can eliminate the nagging about a vulnerable plugin or extension for a little while. Summary No one will disagree that Flash is something that most, if not all, of us can't wait to see go away. No one will disagree that Flash is one of the largest security vulnerabilities on the internet, and possibly of all time. Most people will concede these arguments, and agree with you. But since we're strapped with this albatross for the foreseeable future, it would be nice to not have to put up with the constant nagging from Mozilla about yet another vulnerability that has been discovered, which is every time that Adobe issues another update. These days, it seems they only update Flash when another security vulnerability is discovered, and that's proving to be quite often lately. By all means, keep your PCLinuxOS installation updated regularly. It's the best defense against those security vulnerabilities. But the methods discussed above can keep things running well until you can get around to performing those updates, and help keep the nagging from Mozilla to a minimum. |